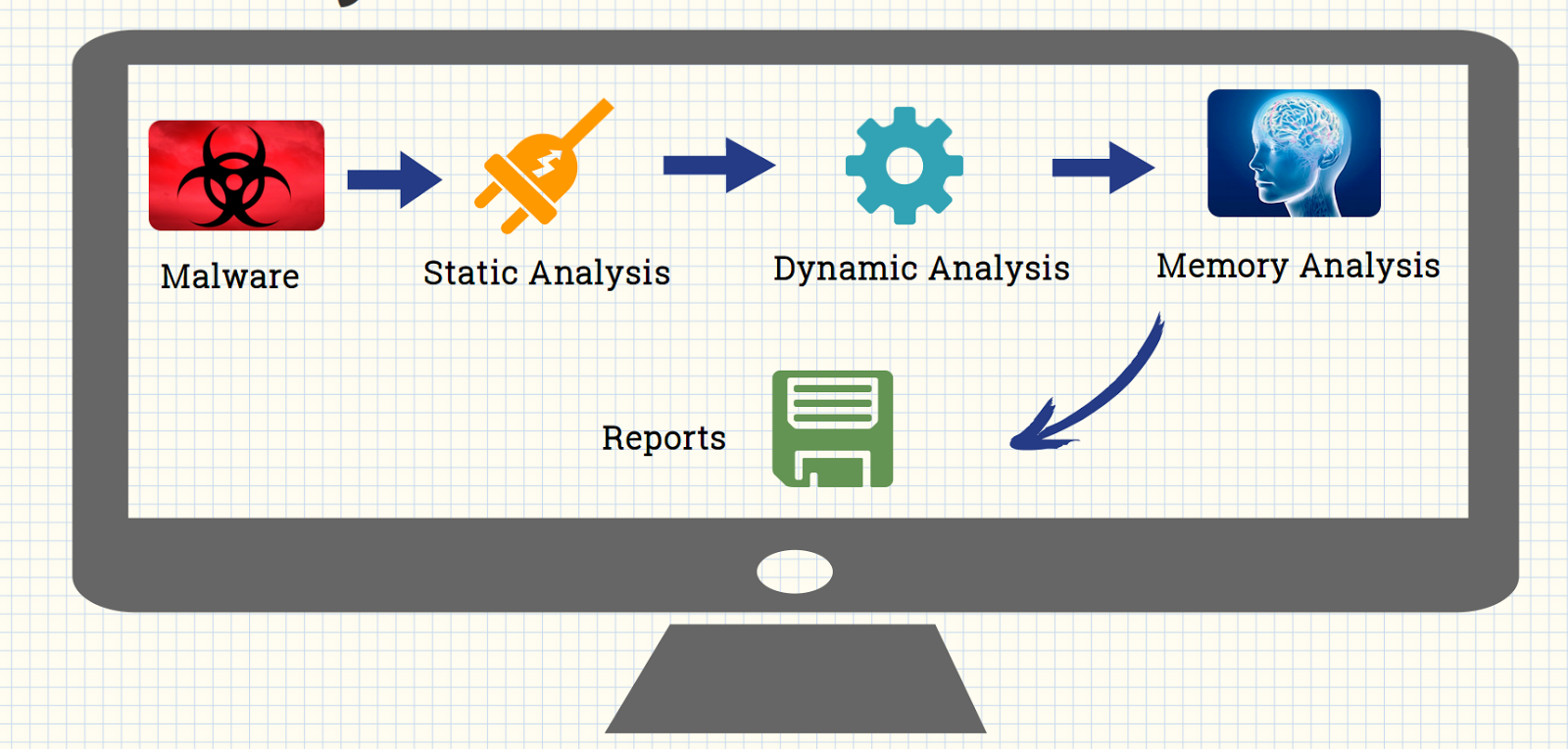
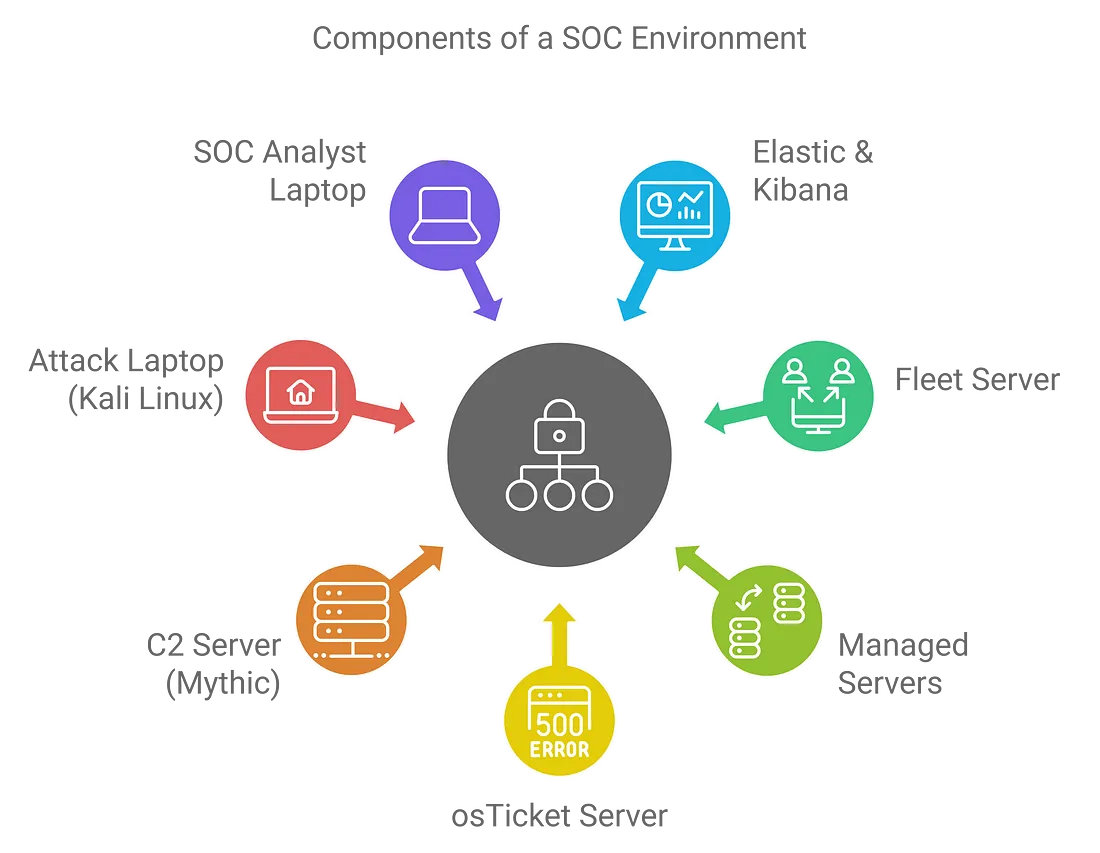
Introduction PART 1️⃣ welcome to part one of five for the series on the active directory project the goal of this project is to start from nothing at all to a fully functional domain environment [...] Read more
Active Directory Lab