- Scenario
You have just started a new role as a Security Consultant for Frozen Yoghurt Limited.
- Name of Company: Frozen Yoghurt Ltd, UK
Description: This company specializes in the in-shop sale of frozen yoghurt brands and delivery within the Portsmouth area in the United Kingdom. Number of staff: Seven
- Roles and responsibilities:
- Two (2) Administrators -.
- Three (3) salespeople;
- One (1) IT Support;
- One (1) Manager.
IT Resources:
One central server hosting mail, public website, internal
documents, and all databases. The central server is physically
located in the shop.- One Windows device and a tablet device in the shop, with access to
the central server - • Remote connections for three members of staff.
- • Electronic document and records management (EDRM) system; human resources (HR) system; customer database; providers database; sales database; stock inventory system.
Frozen Yoghurt’s central server has been recently compromised, and files stolen from its servers. Fortunately, the following log files were recovered:
- • Network capture in a PCAP format
- • Firewall logs
- • IDS logs
• Server logs
Download the log files below: (These have been provided)
- auth
- • kern
- • Network Packet Capture
- • Suricata logs
• syslog
****Task****
You are required to do the following: Investigate the incident and produce a detailed report. Include:
- What, how and when it happened
- Graphical timeline of events
- Analysis of suspicious and malicious events extracted from the PCAP and logs (describe the objectives)
- Recommendations for securing the system.
Evidence of investigation / analysis, for example, screenshots, code snippets
Develop a risk assessment strategy to mitigate future events. Use
examples from the scenario to show how your plan will foil the
previous attack. Note
To do the tasks above, you may need to make some assumptions. Please highlight them in your report.
- Incident Overview
Company Name: Frozen Yoghurt Ltd Frozen Yoghurt Ltd. is a small business based in Portsmouth, UK, specializing in the sale and delivery of frozen yoghurt. It operates with a central server hosting critical systems such as email, website, internal documents, and databases for HR, sales, stock inventory, and more. Recently, the company experienced a security breach where files were stolen from the central server. As a new Security Consultant, your task is to investigate the incident and provide a detailed report along with recommendations to mitigate future risks.
. What, How, and When It Happened
What Happened:
The system with IP address 192.168.56.1 was compromised and attempted to establish a connection with the central server, which hosts all the critical infrastructure of the business. It connected to 192.168.56.102 on port 80 and successfully established a connection on port 23 at 14:34:53. This occurred after a legitimate access to the server, during which a cron job was triggered. The job initiated a brute-force attack with multiple requests. After several minutes, it successfully gained access to the server, used sudo commands to view staff information, and then exfiltrated the data.
- How It Happened:
On March 8, at 14:24:26, a session was opened by a legitimate user, during which they executed system management commands, such as checking the status of Suricata and managing iptables. They also started Wireshark to capture network traffic. After the legitimate user's session ended, I observed a cron job being executed.
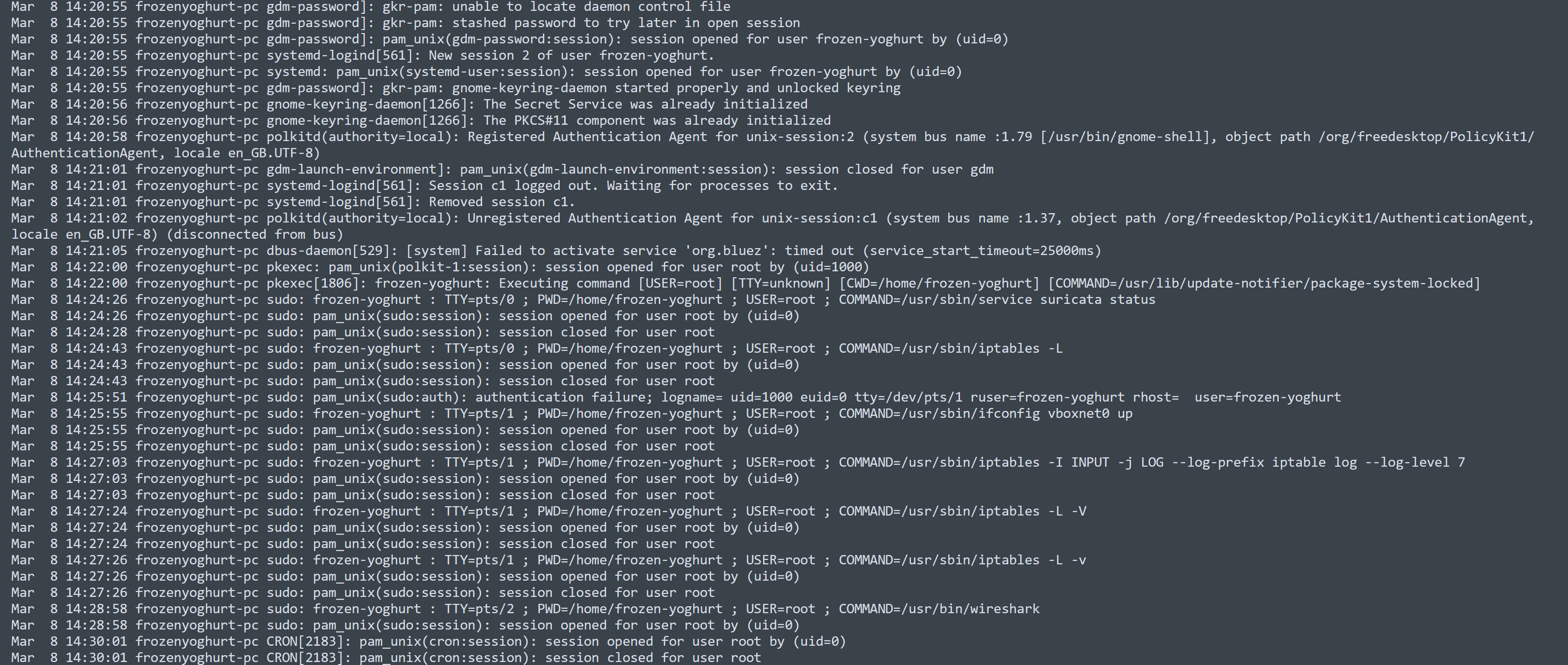
Shortly afterward, there were multiple failed login attempts originating from 1.capita.vpn.port.ac.uk and the IP address 192.168.56.1.
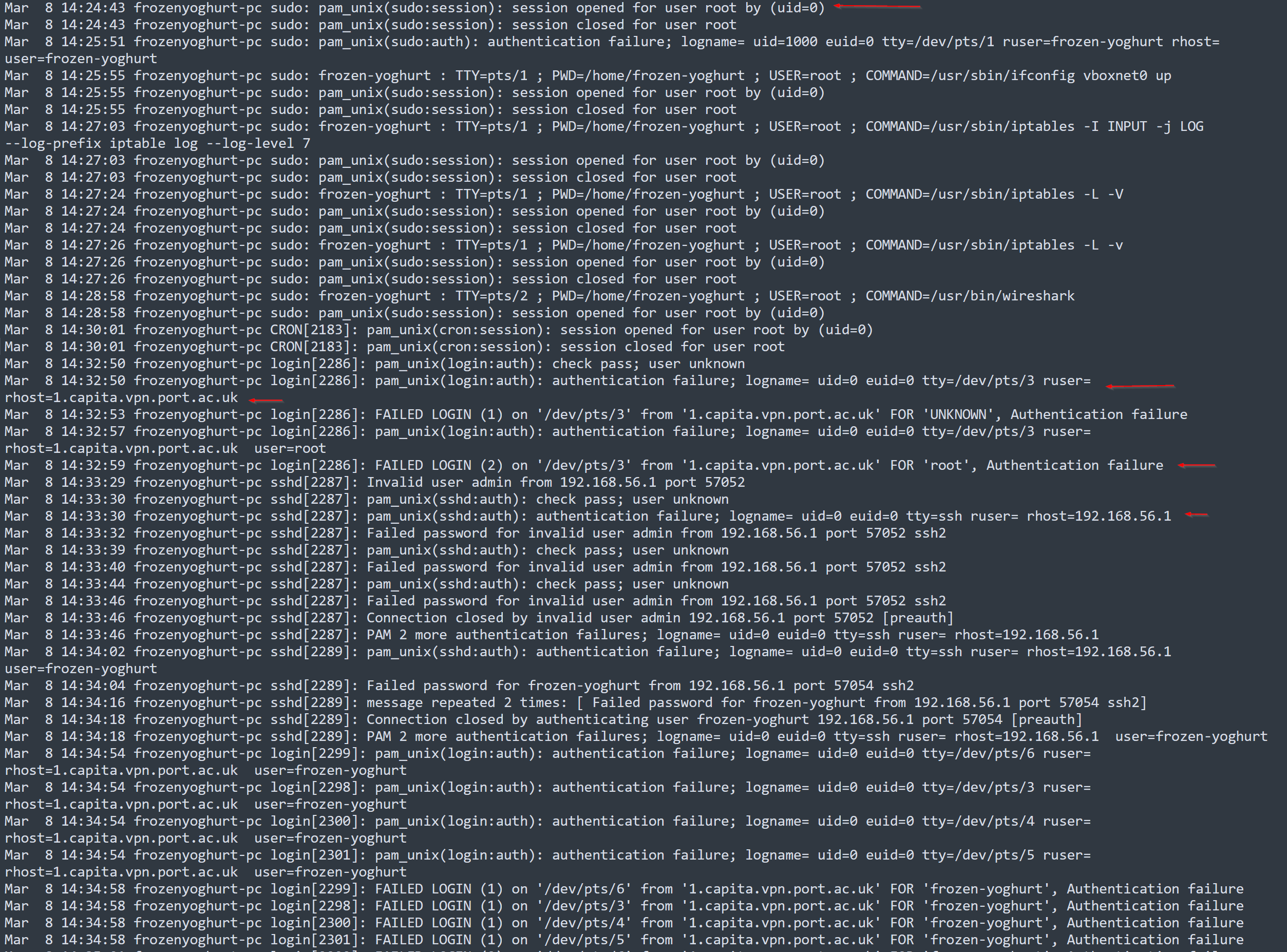
1.capita.vpn.port.ac.uk finally gained accessed into the Central Server
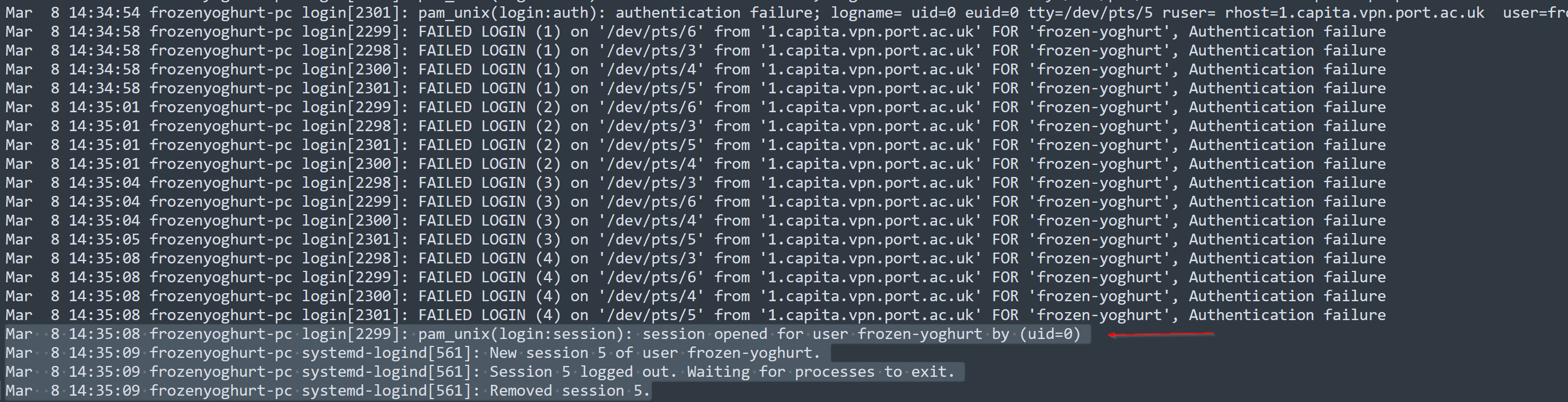
- IDS Logs: There are multiple attempts between 192.168.56.1 (source) and 192.168.56.102 (destination), particularly targeting port 23 (TELNET). Multiple entries show source IP 192.168.56.1 attempting different source ports to connect to the same destination.
The ICMP connection attempts between 192.168.56.1 and 192.168.56.102 suggest that the compromised host is probing the network to verify connectivity with other devices, likely as part of a reconnaissance effort. The server’s response indicates that it is reachable, which may lead to exploitation activities from the attacker.
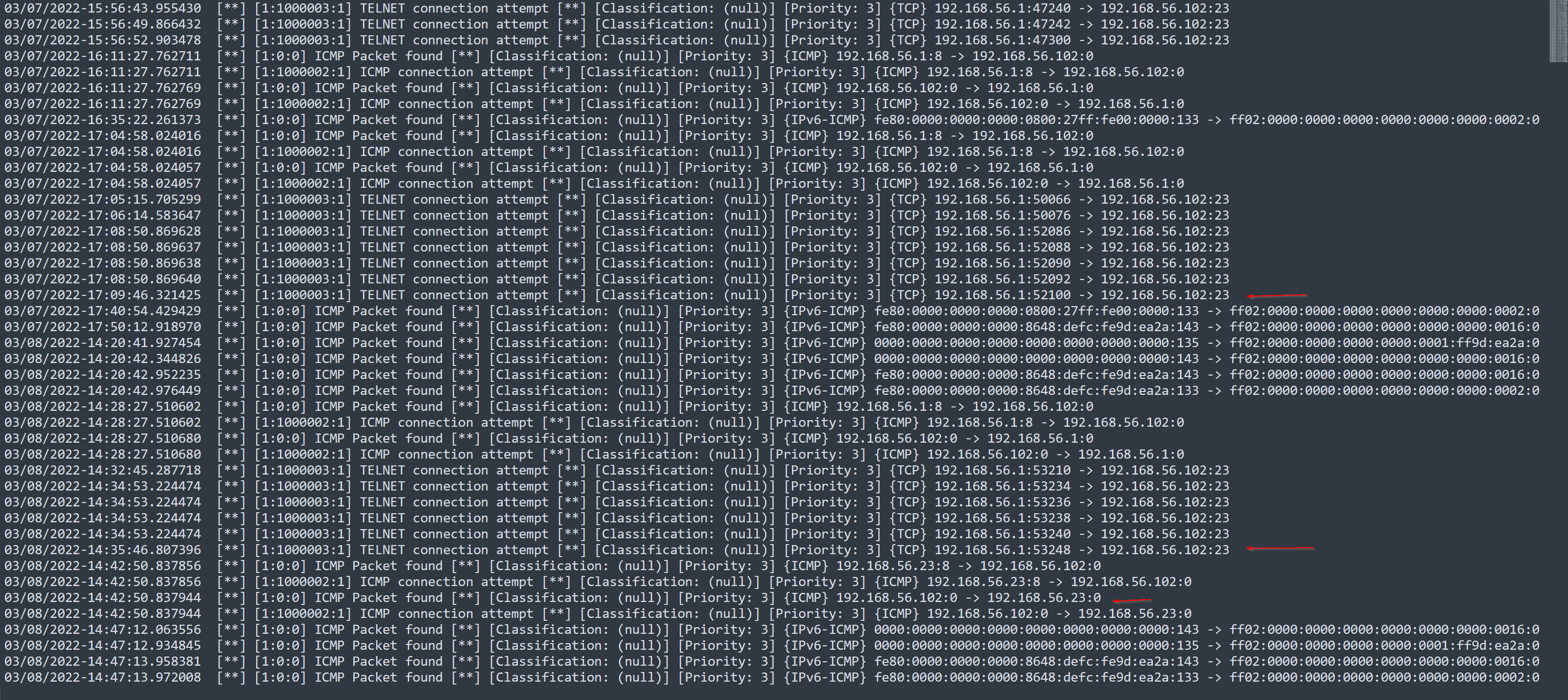
- Syslog
During the three-way handshake, the source IP (192.168.56.1) sent a SYN packet to the destination IP (192.168.56.102) on port 23, followed by an ACK from the destination to confirm the connection, and finally, the source IP sent an ACK to complete the handshake.
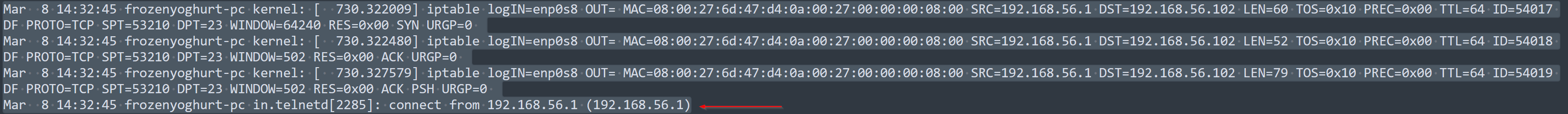
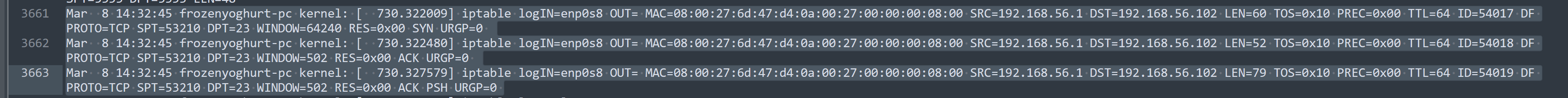
- Kern
This also confirm the syslog by showing the exact time which the system was sign in to. 14:32:45
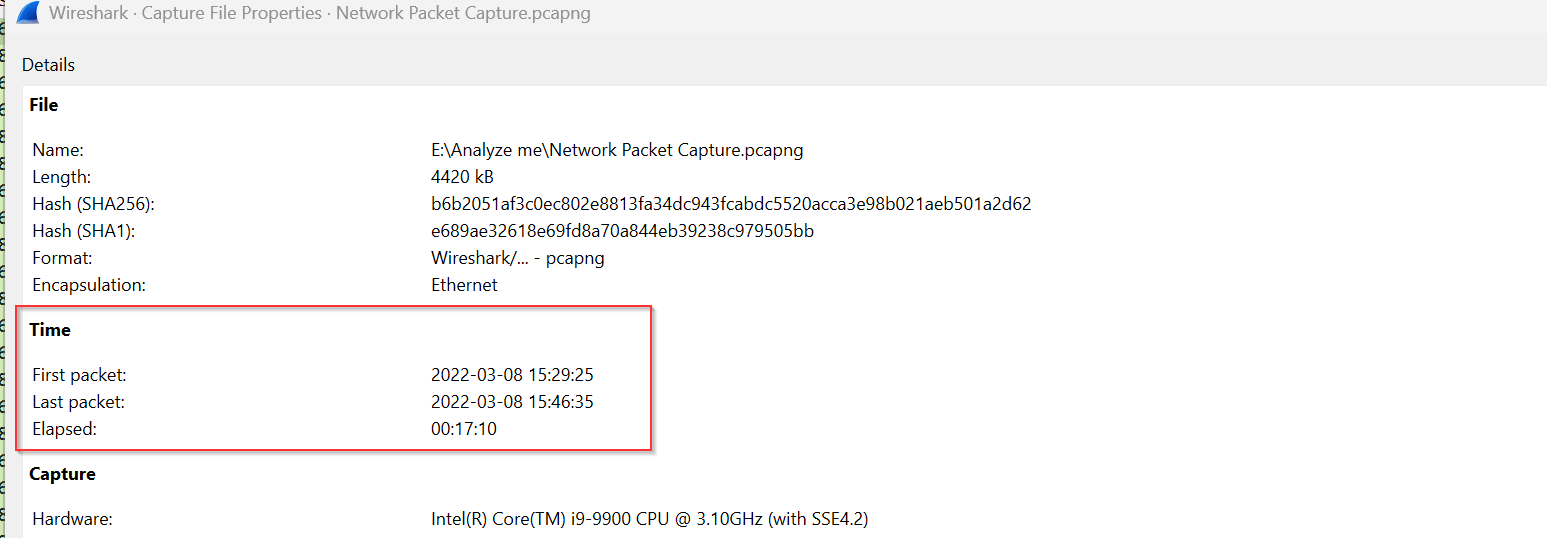
- Network Traffic Analysis:
From checking the pcap properties the time match with other time on other logs provided this will give insight into what really happened and if any data was exfiltrated
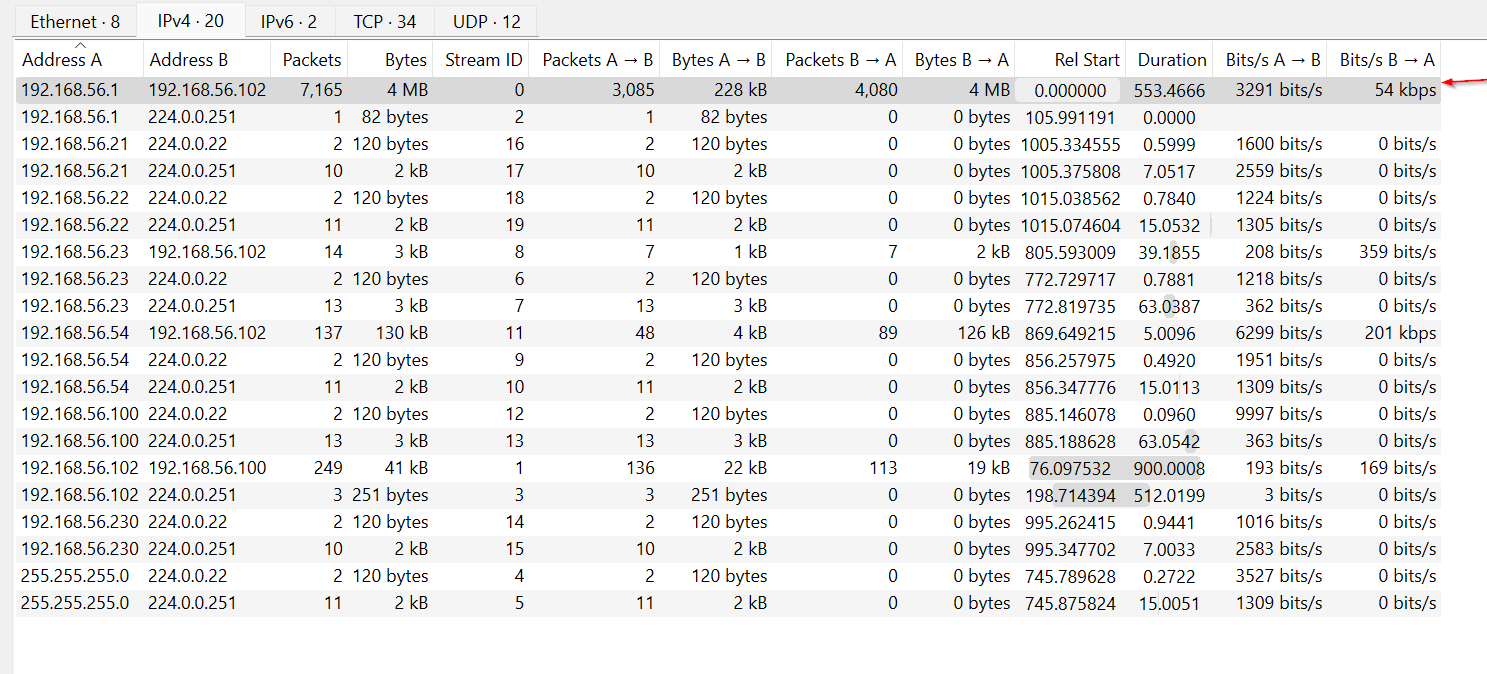
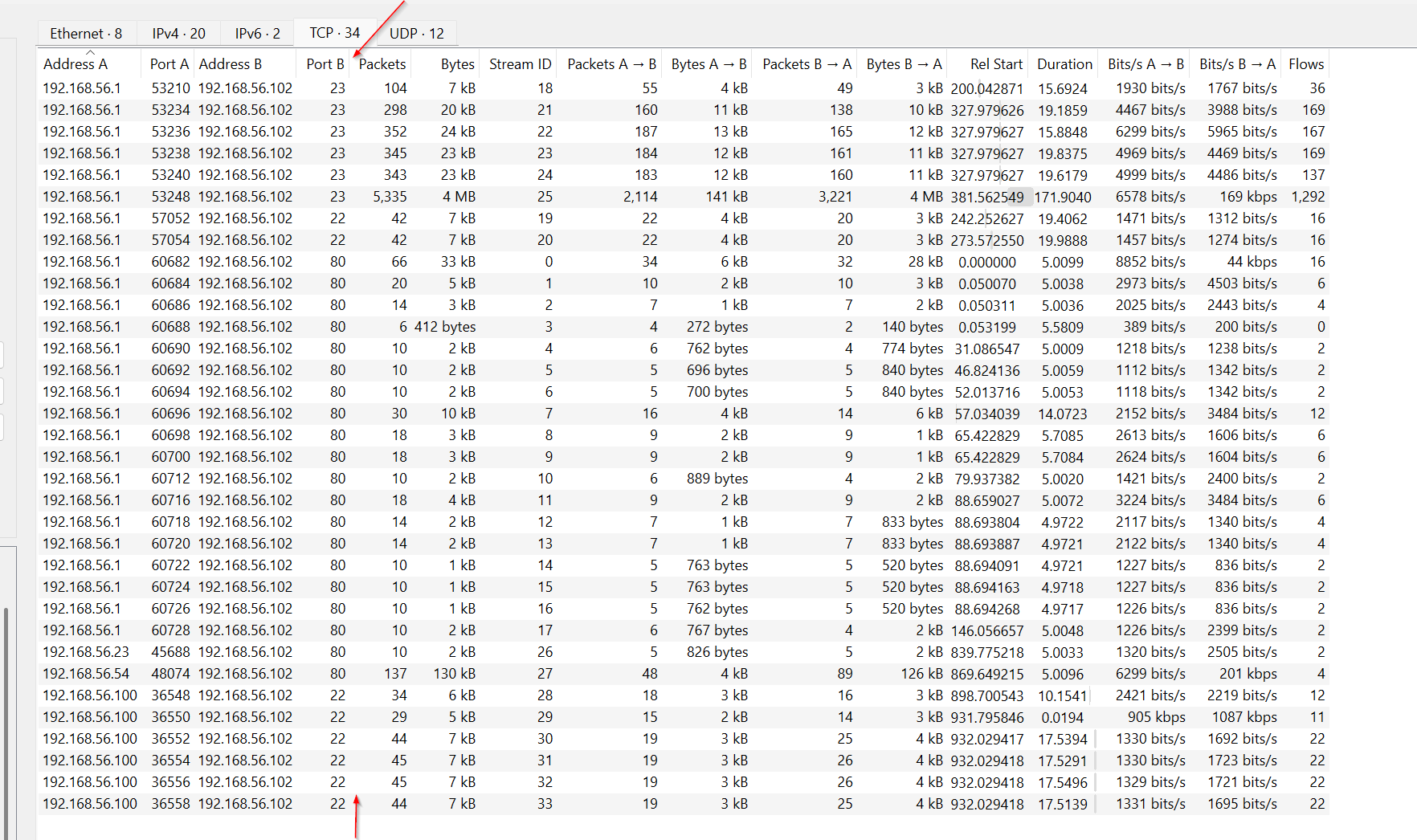
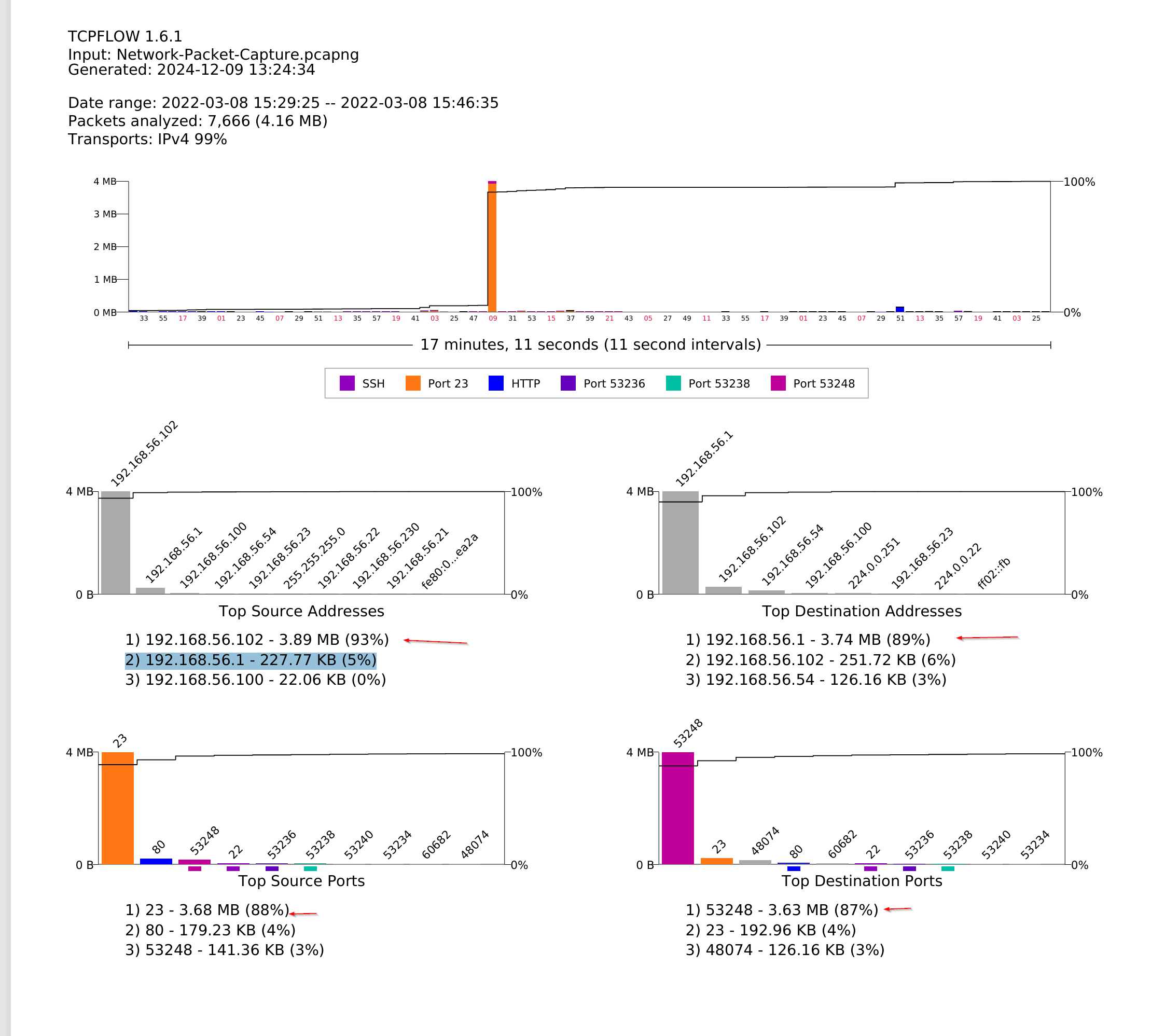
The conversation between Device A (192.168.56.1) and Device B (192.168.56.102) stands out as it involves the highest number of packets and bytes transferred in this network capture.
Packets A → B: Device A sent 3,085 packets to Device B, totaling
approximately 228 KB of data. - Packets B → A: In response, Device B sent 4,080 packets, accounting for around 4 MB of data back to Device A. Device A to Device B: The traffic from Device A to Device B is observed to have a data rate of 3,291 bits per second. Device B to Device A: On the other hand, traffic from Device B to Device A has a higher rate of 54,000 bits per second (54 kbps). This could indicate that Device B is not just responding to requests but is also sending significant data back, possibly in larger data blocks or in response to ongoing processing requests made by Device A.
With the information on opened port on device B clearly it running a central server with open ports for Web Server, Telnet, and SSH. Device A used random ports this clearly show it a scanning attempt on the centra server.
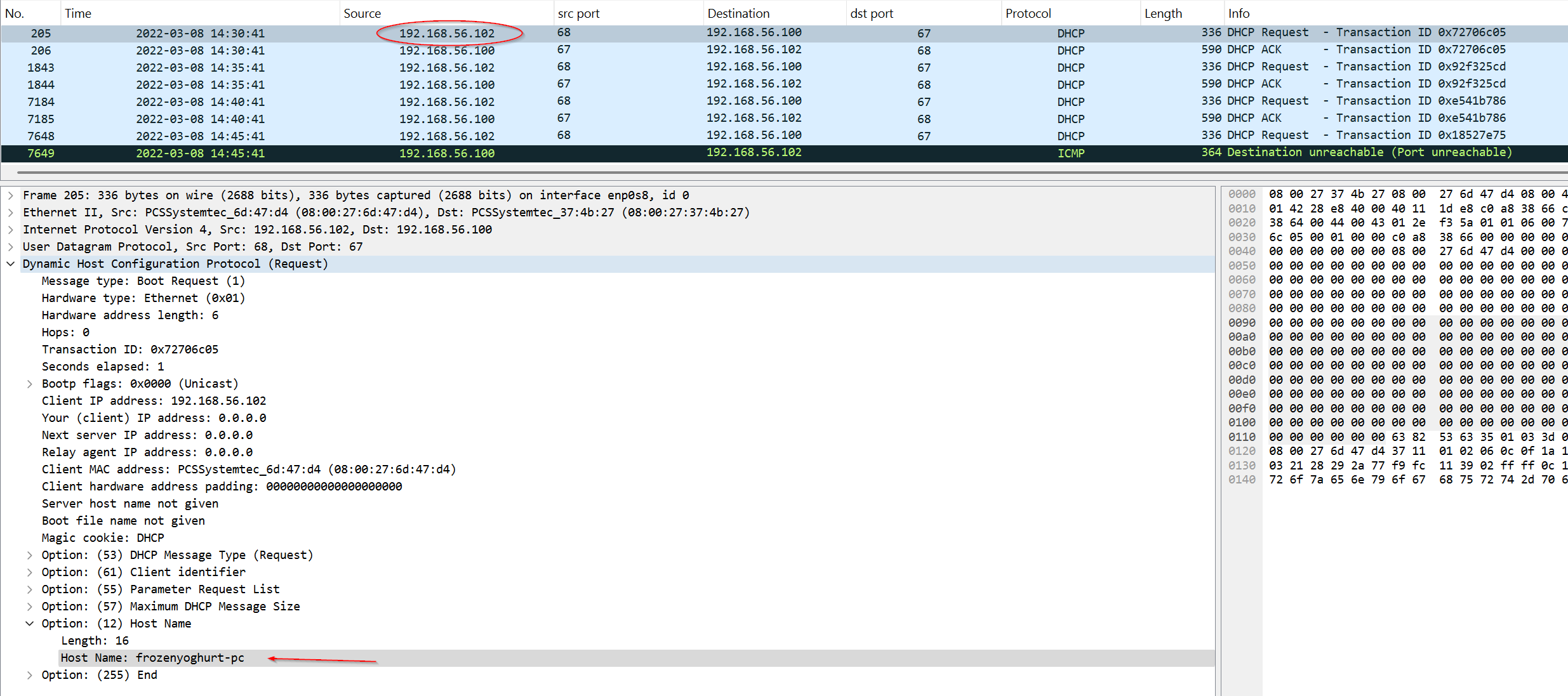
The device on 192.168.56.102 host name is frozenyoghurt-pc this confirm it the central server again.
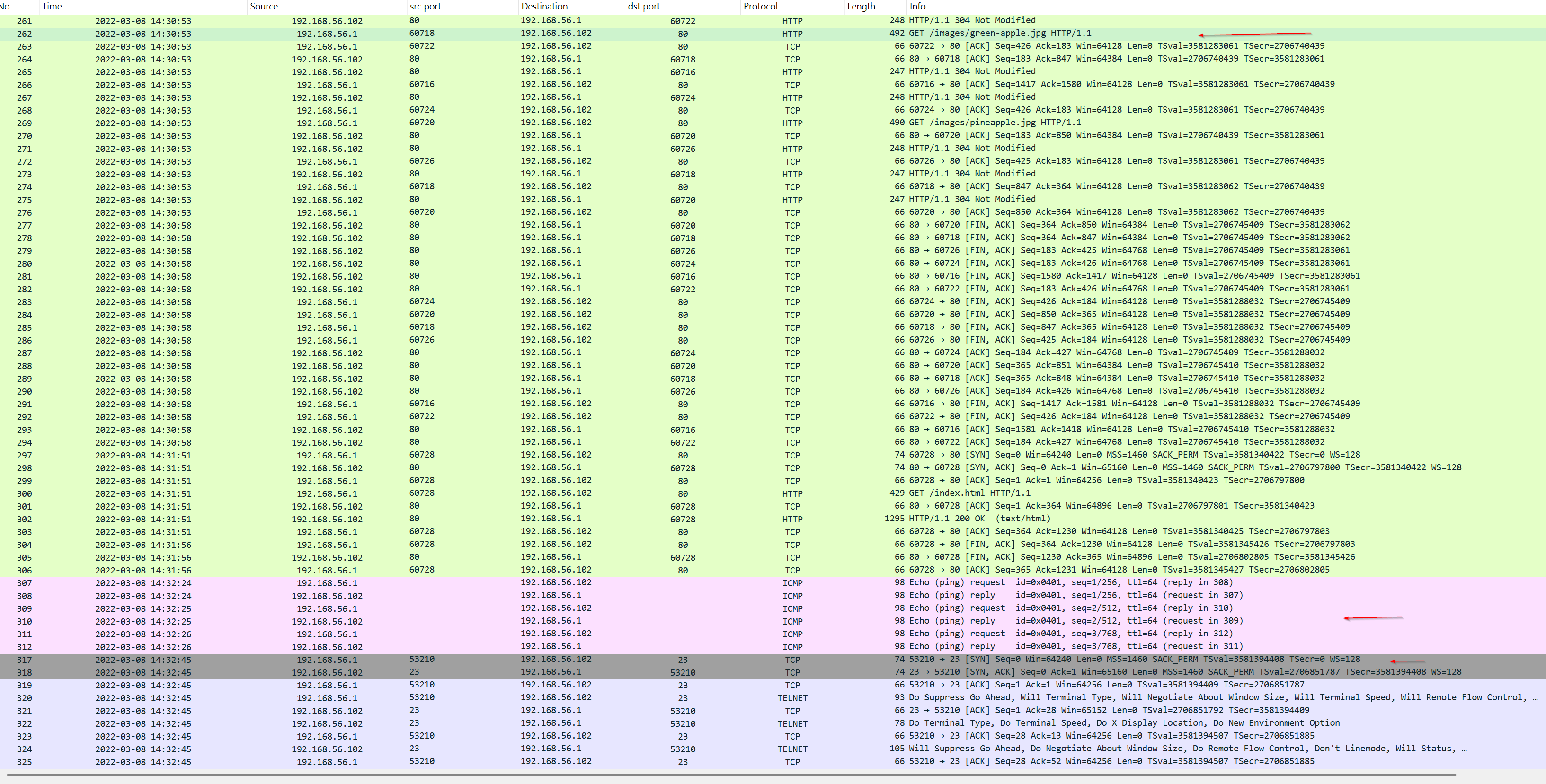
The devices are engaged in web browsing activity (HTTP), Telnet session initiation, and basic network diagnostics (ICMP ping) that was showed ealier from the IDS logs.
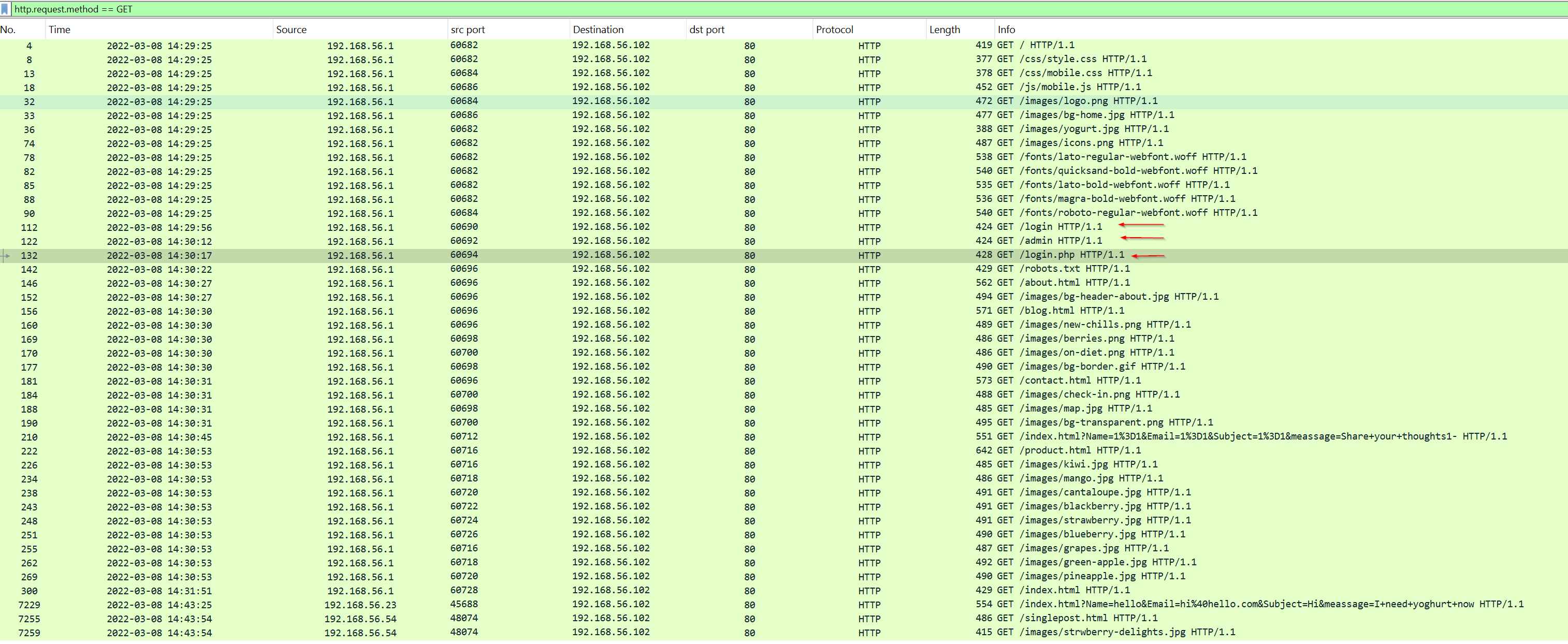
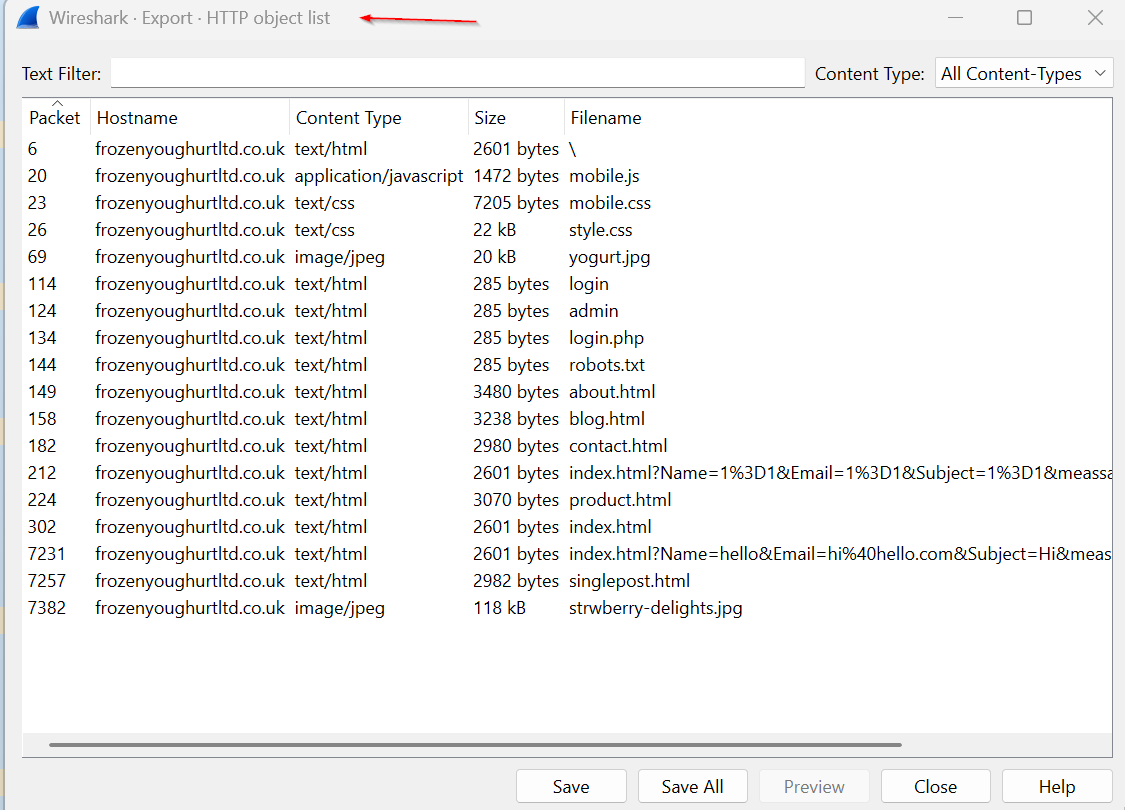
There was multiple http GET request made to the webserver but there was no POST
The password frozen was use by the attacker to accessed the server and we could see the last login was made at Mar 8 14:35:08 by
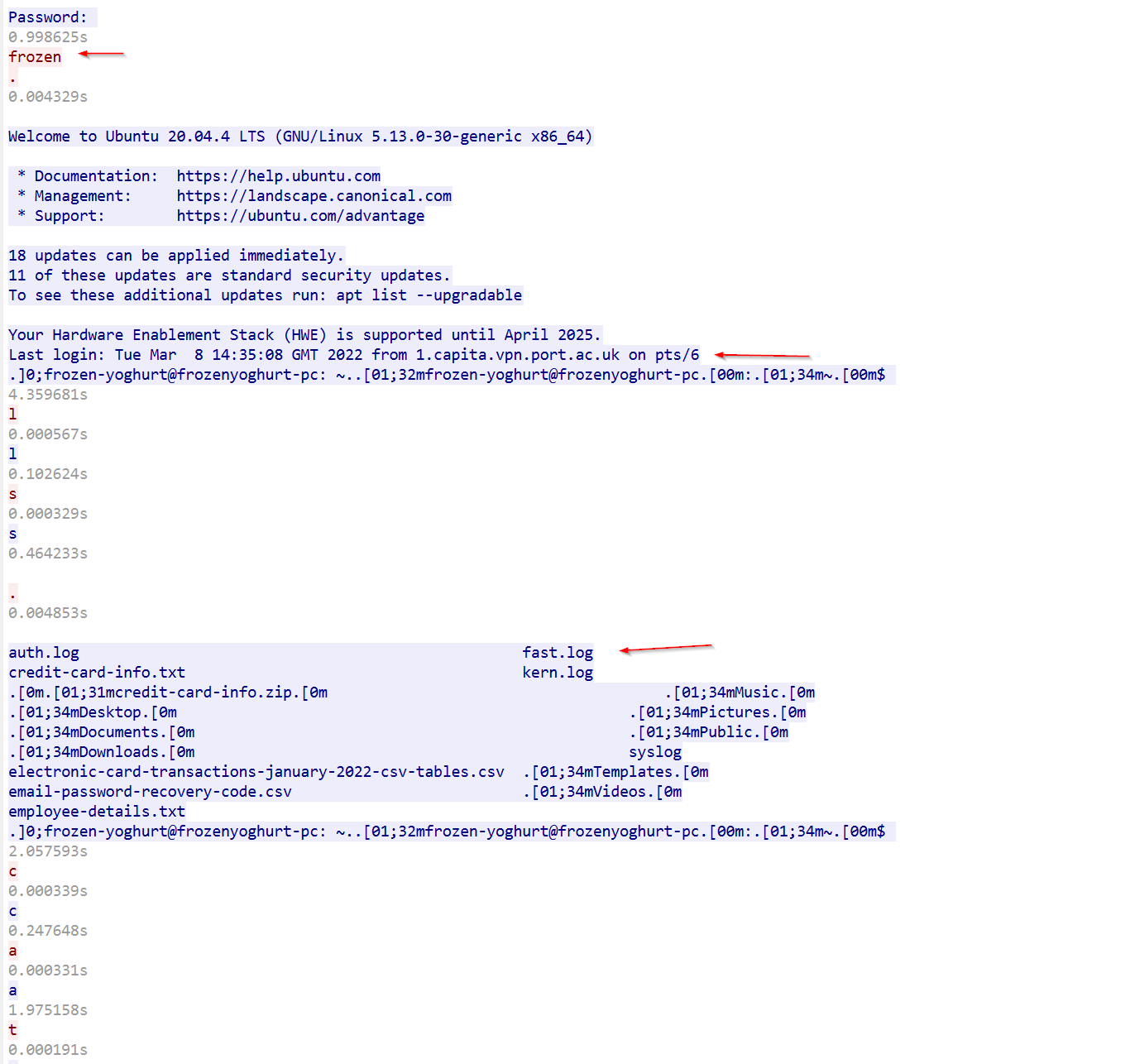
EXFILTRATED DATA : Analysis from TCPFLOW shows 93% of packet was transferred from 192.168.56.102 3.89 MB (93%)
Export Objects were filled with the https response from the server which consists of the home page and login page that was requested by the client.
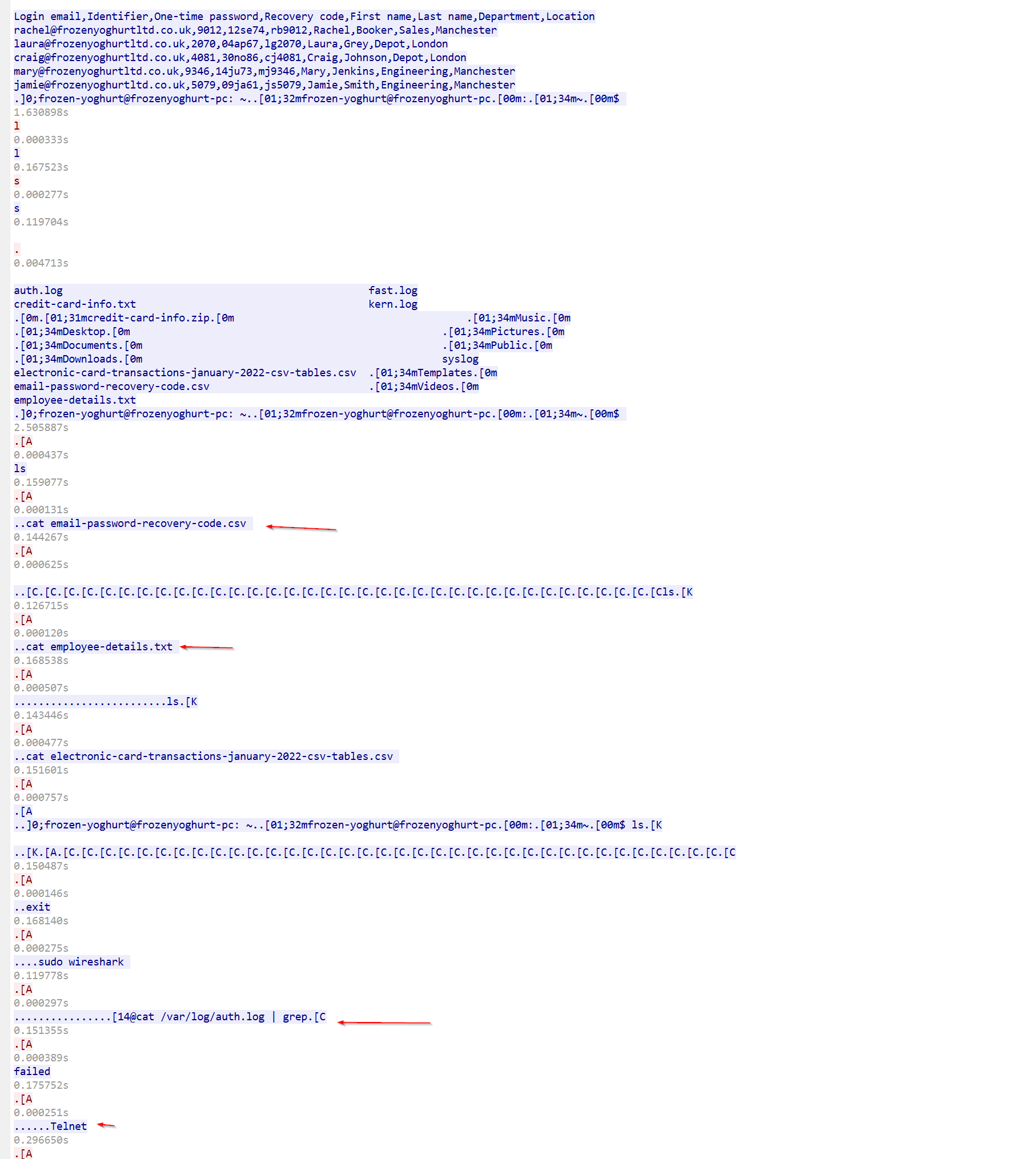
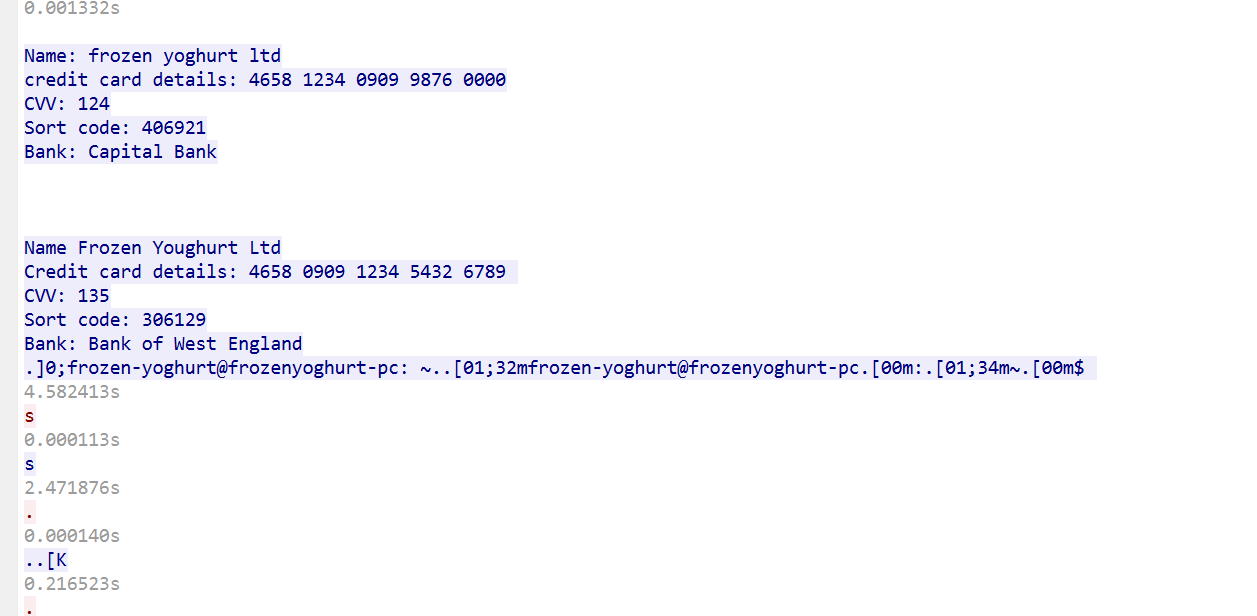
Employee Information was displayed and exfiltrated
 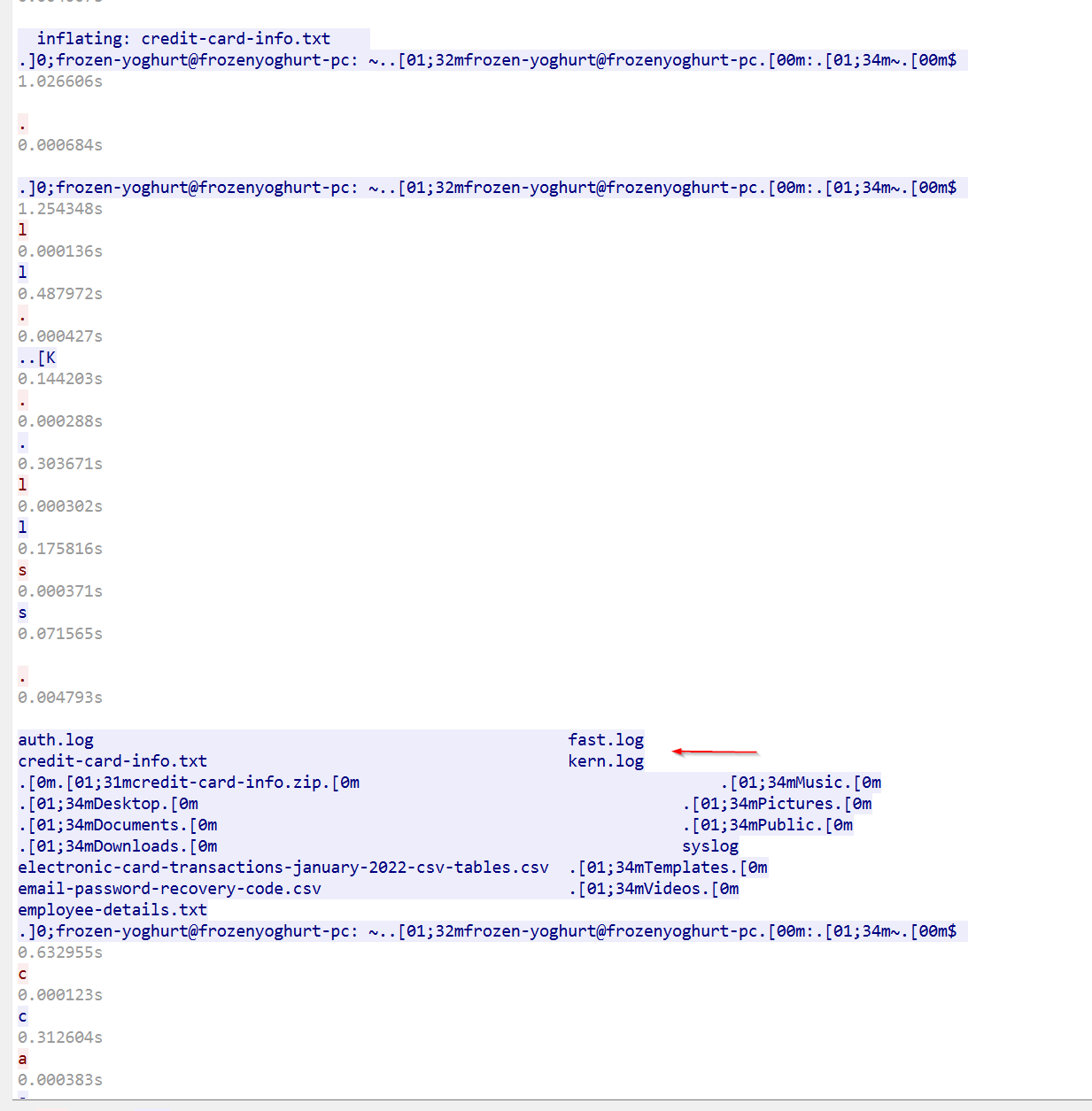 ]
]
2. Develop a risk assessment strategy to mitigate future events. Use
examples from the scenario to show how your plan will foil the
previous attack.
- Risk Identification
The following risks were identified in the scenario:
- Unauthorized Access: Attackers successfully gained access to the central server by exploiting weak authentication, including brute-force attempts and lack of proper access control
- Weakness in Network Configuration: The system used insecure protocols like Telnet (port 23), which were exploited during the attack
- Vulnerability to Brute Force Attacks: Weak passwords was used in the attack, making the system vulnerable to brute-force and dictionary-based attacks.
Exfiltration of Sensitive Data: Sensitive data, including employee and customer information, was exfiltrated by the attacker, indicating poor data protection and monitoring.
Risk Mitigation Plan
Based on the identified risks, here’s a comprehensive risk mitigation plan to reduce the likelihood of a similar incident occurring in the future:
- Require employees to use strong, complex passwords
- Replace Telnet (port 23) with Secure Shell (SSH) for remote access, as SSH encrypts the connection and reduces the risk of password sniffing.
- Use HTTPS for all web traffic and ensure that SSL/TLS certificates are properly configured to encrypt data in transit.
- Implement a properly configured firewall that blocks unnecessary inbound and outbound connections, particularly for ports not in use
Enable real-time monitoring to detect suspicious behavior, such as multiple failed login attempts, abnormal network traffic, and changes in server configurations.
- Conclusion By implementing these recommendations, Frozen Yoghurt Ltd can reduce the risks associated with unauthorized access, data exfiltration, and poor network security. A combination of strong authentication mechanisms, secure data practices, robust network monitoring and employee training will help to create a secure environment.

