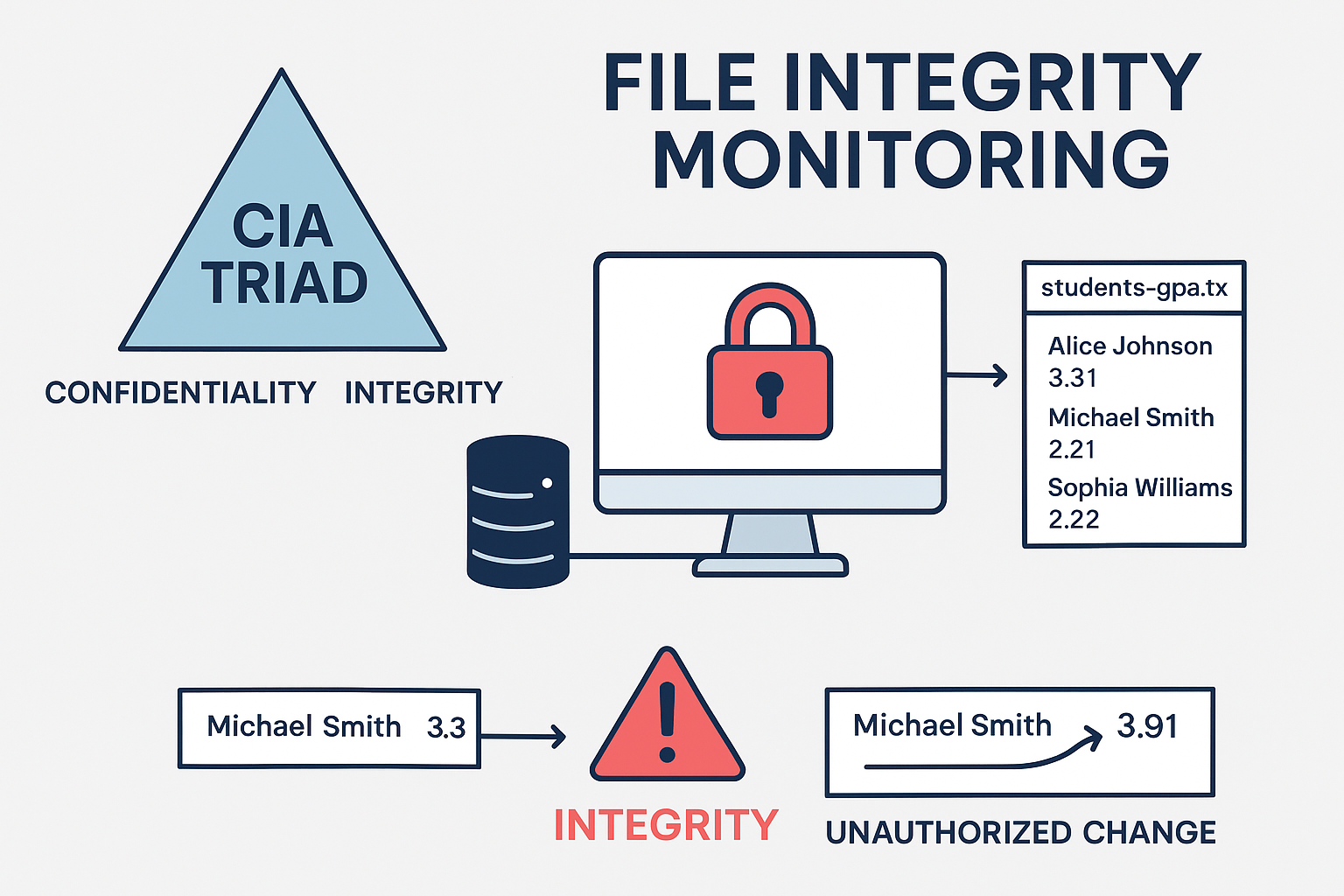
What is the CIA Triad? The three letters in "CIA triad" stand for Confidentiality, Integrity, and Availability. The CIA triad is a common model that forms the basis for the development of security [...]

Forensicfossil
SOC Analyst Blog