NETSTAT
In today's digital world networks connect everything. Whether you're fixing connection problems checking system performance or looking into suspicious activity understanding network traffic is key. One useful tool for this is the netstat command.
In this blog post, we’ll break down netstat—how it works, its advanced features, and why it’s so important for forensic investigation and network issues.
What Is Netstat?
Netstat (short for “network statistics”) is a command-line tool built into most operating systems—Windows, Linux, macOS. You can use in Command Prompt to display statistics for all network connections. It allows you to understand open and connected ports to monitor and troubleshoot networking problems for systems or apps. The tool helps you to list active network (incoming and outgoing) connections and listening ports. You can view network adapter statistics and statistics for protocols (such as IPv4 and IPv6). You can even display the current routing table and much more.
Understanding Connection States
- LISTENING: A port is open and waiting for incoming connections (e.g., a web server listening on port 80).
- ESTABLISHED: An active, two-way connection between your device and another (e.g., your browser talking to a website).
- TIME_WAIT: A temporary state after a connection closes. The system keeps it briefly to ensure no leftover data arrives.
- CLOSE_WAIT: The remote side closed the connection, but your local app hasn’t yet. Often points to a misconfigured app.
- SYN_SENT: Your device sent a connection request (SYN packet) but hasn’t received a reply yet.
What Does 0.0.0.0:Port Connections Mean? You may encounter entries with IP addresses and ports listed as 0.0.0.0:0 or similar. Here’s what they indicate:
0.0.0.0 in the "Local Address" column means the service is listening on all network interfaces (Wi-Fi, Ethernet, etc.).
Listening on 0.0.0.0: When a server is “listening” on 0.0.0.0, it’s ready to accept connections from any IP address, ensuring flexibility and broad accessibility. This is common for servers intended to serve multiple clients across different networks.
You can quickly view the available options on your Linux system by running:
netstat -h
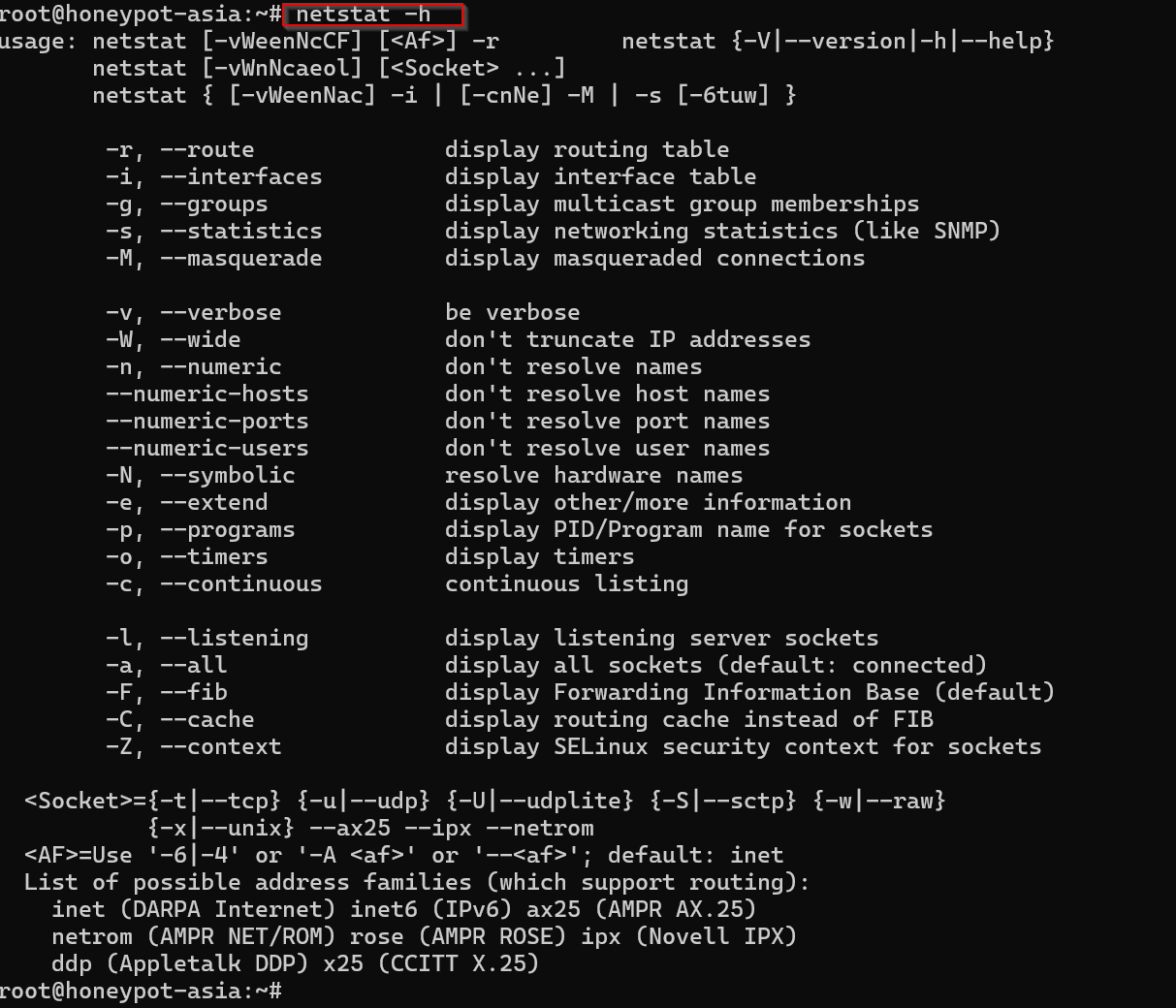
Basic Usage: Getting Started Show Both Listening and Non-listening Sockets Using netstat Command in Linux,
netstat -a
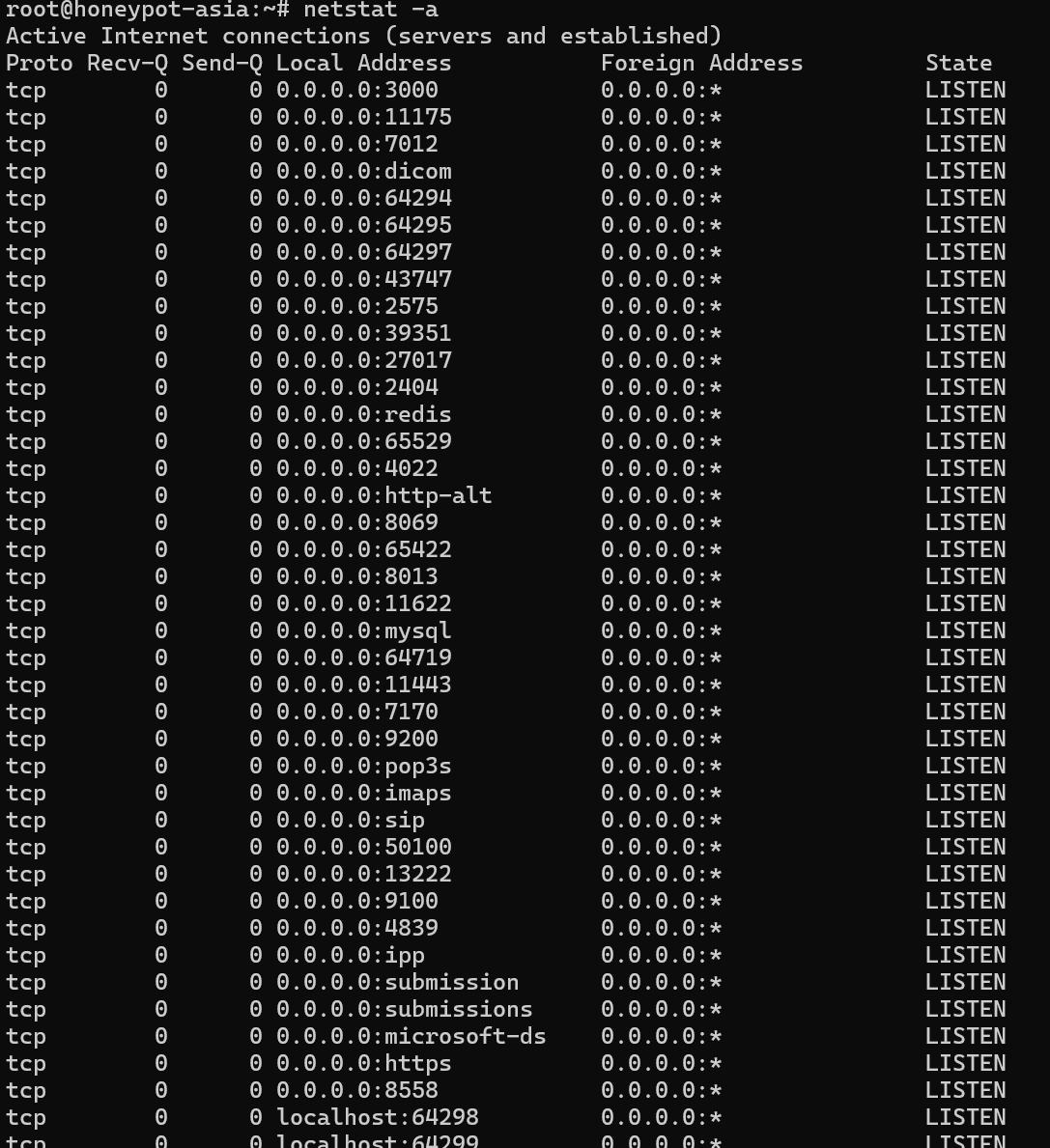
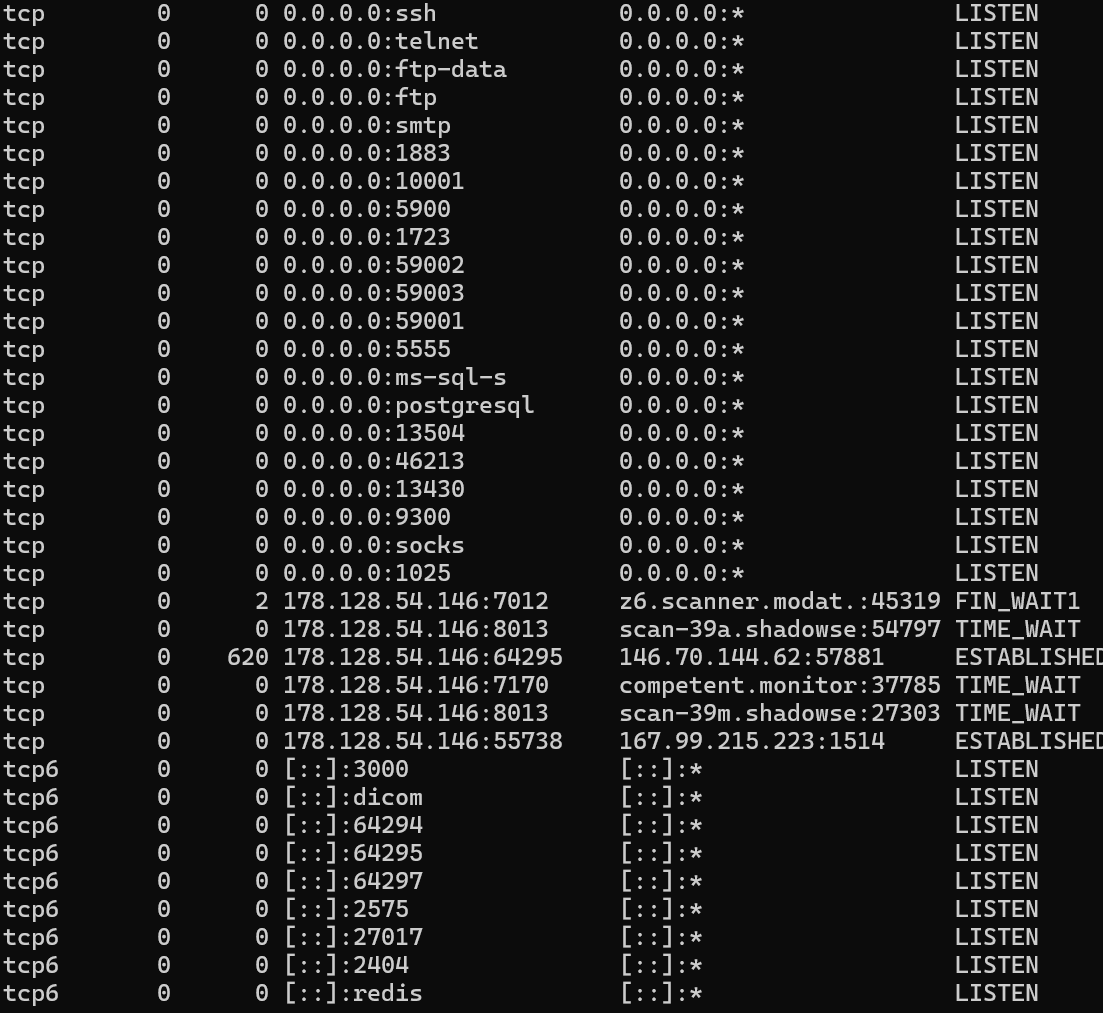 This command lists every active connection and all ports currently listening for incoming traffic, with the –interfaces option, show interfaces that are not up.
This command lists every active connection and all ports currently listening for incoming traffic, with the –interfaces option, show interfaces that are not up.
The -t option specifically displays only TCP connections.
netstat -t
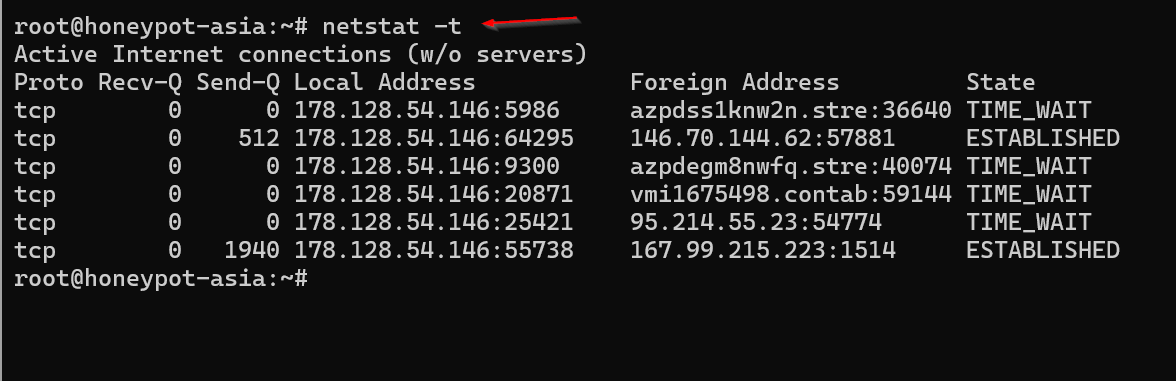
List All TCP Ports Using netstat Command in Linux
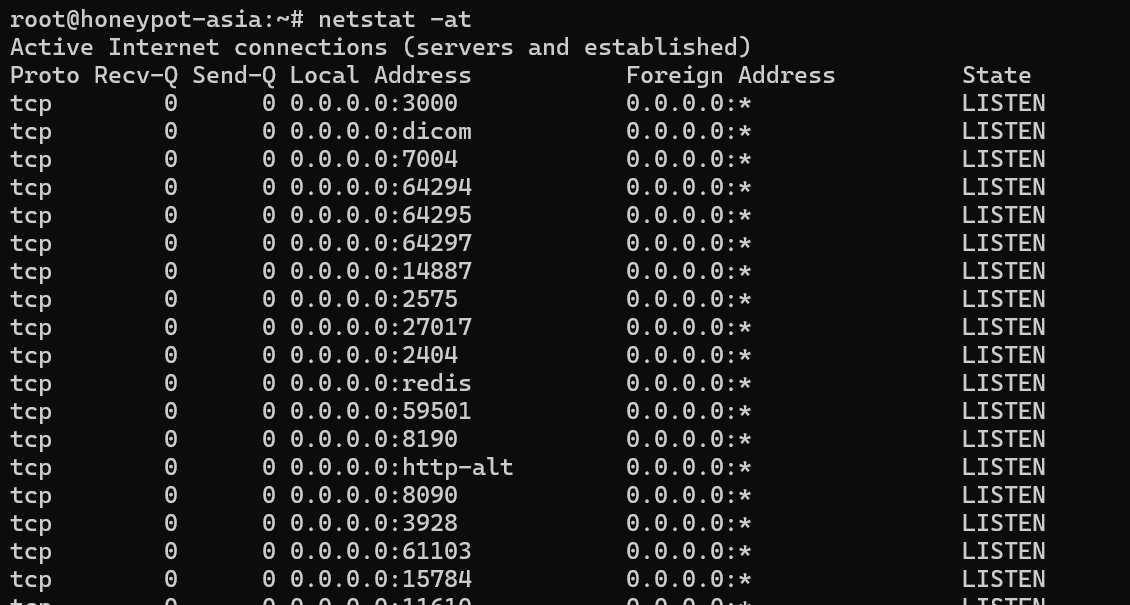
netstat -at
This command specifically lists all TCP ports, giving you information about the TCP connections your system is engaged in.
List All UDP Ports Using netstat Command in Linux
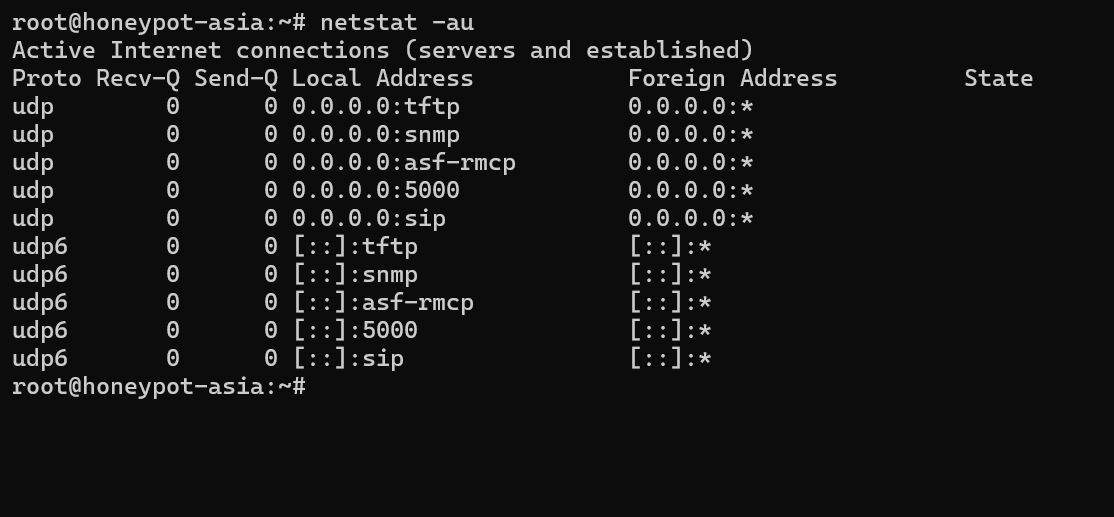
Similar to the previous example this command focuses on UDP ports revealing details about UDP connections
netstat -au
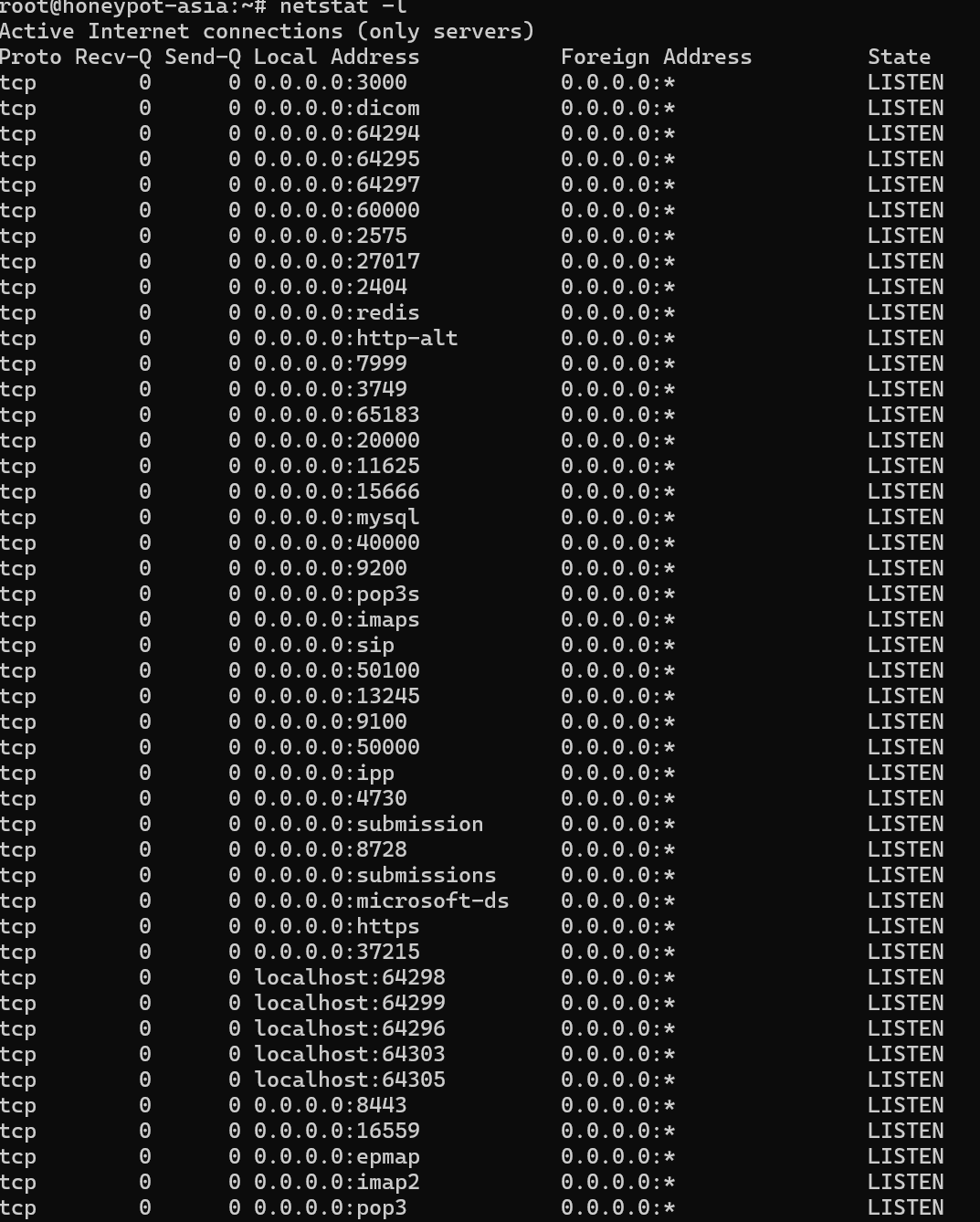
List Only Listening Ports Using netstat Command in Linux It focuses specifically on listing only those network ports that are currently listening for incoming connections.
netstat -l
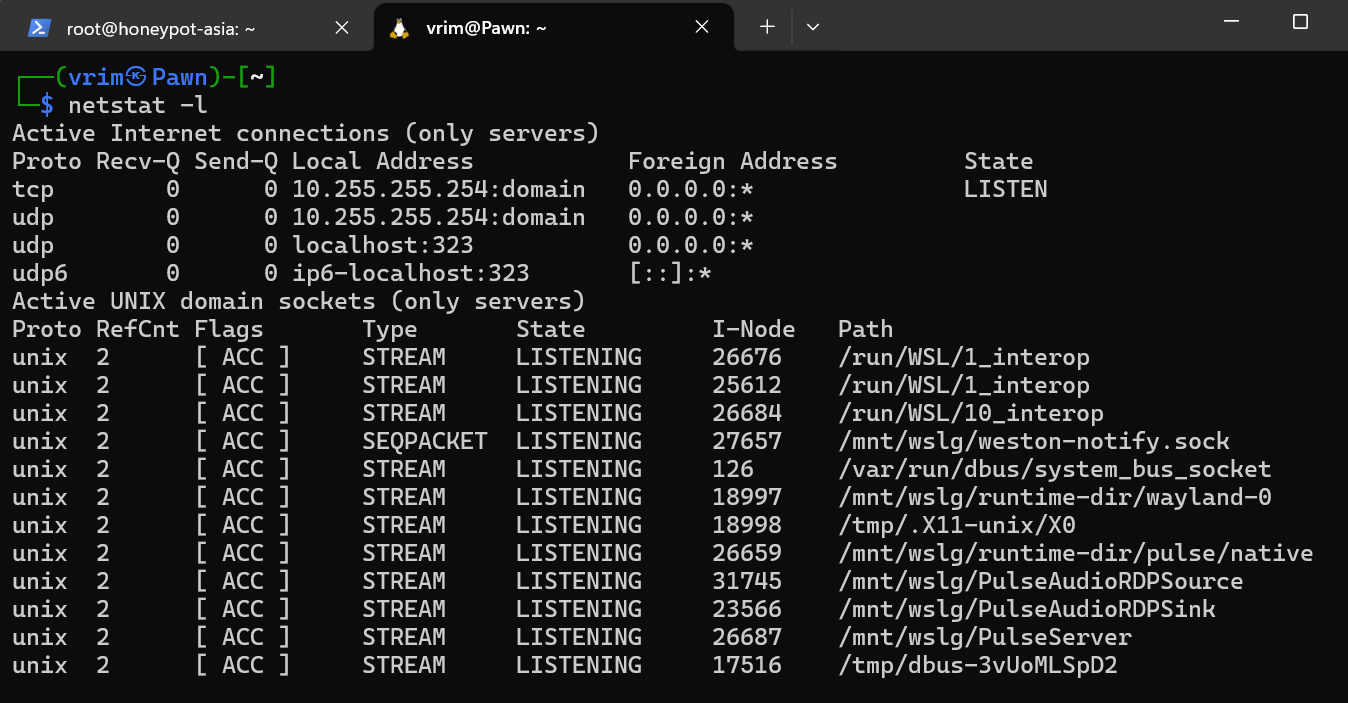
No DNS resolution The netstat -n command displays network connections, routing tables, and interface statistics using numerical addresses rather than resolving hostnames. This means you get a faster, more direct view of IP addresses and port numbers, which is particularly useful when you need quick insights or are troubleshooting network issues without the delay of DNS lookups.
netstat -n
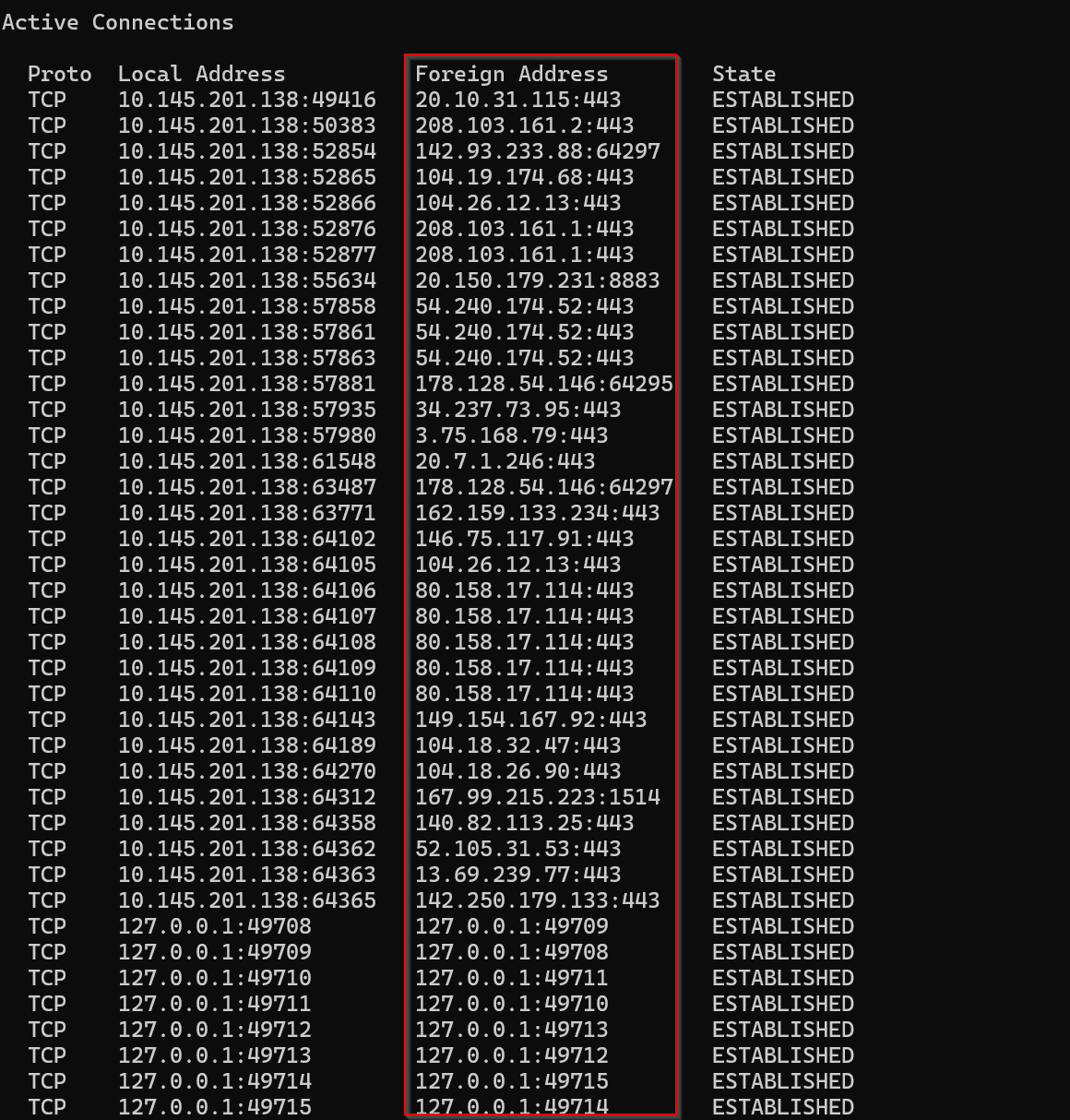
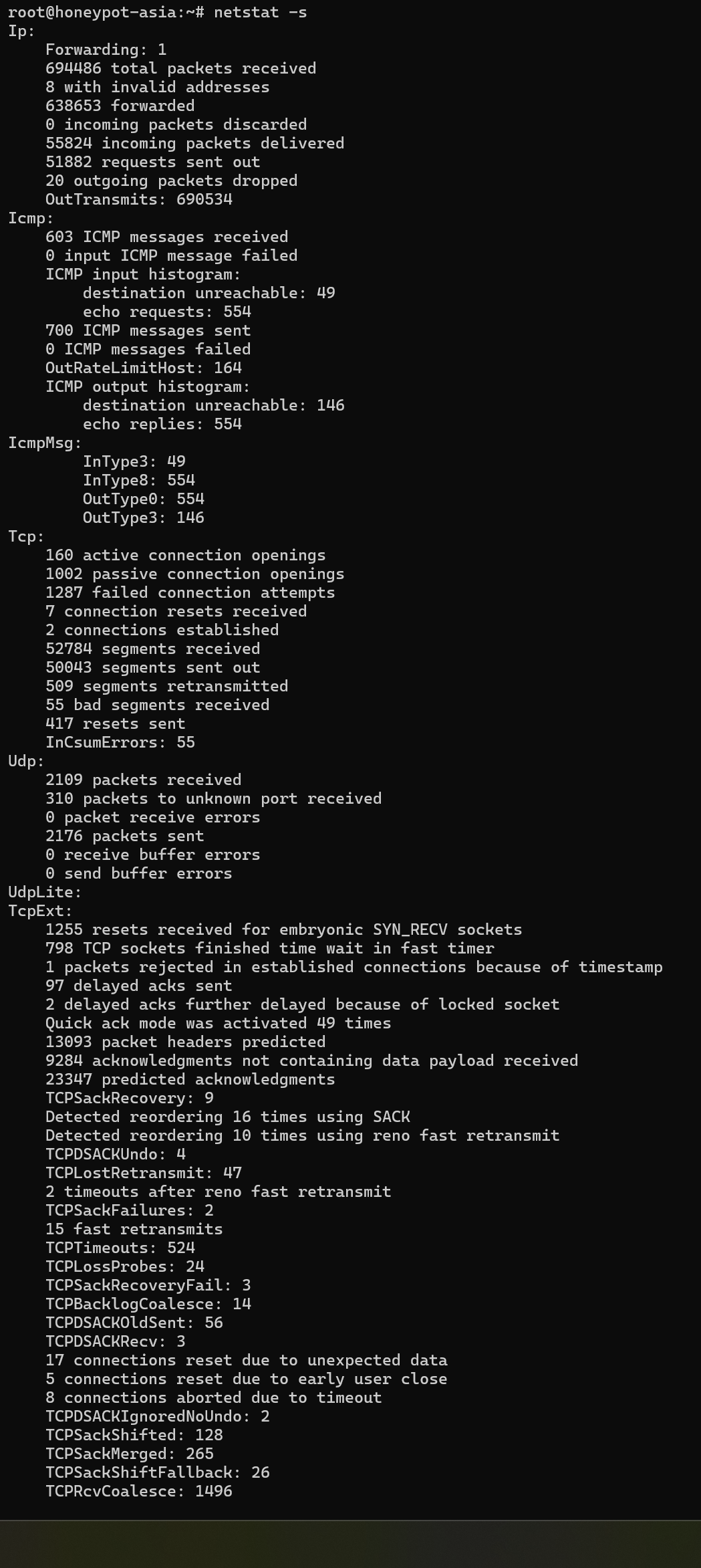
**List Statistics for All Ports Using ** The netstat -s command provides a detailed statistical summary of network protocol activity on your Linux system. When executed it displays counts of various network events, errors, and packet statistics across different protocols (TCP, UDP, ICMP, etc.).
netstat -s
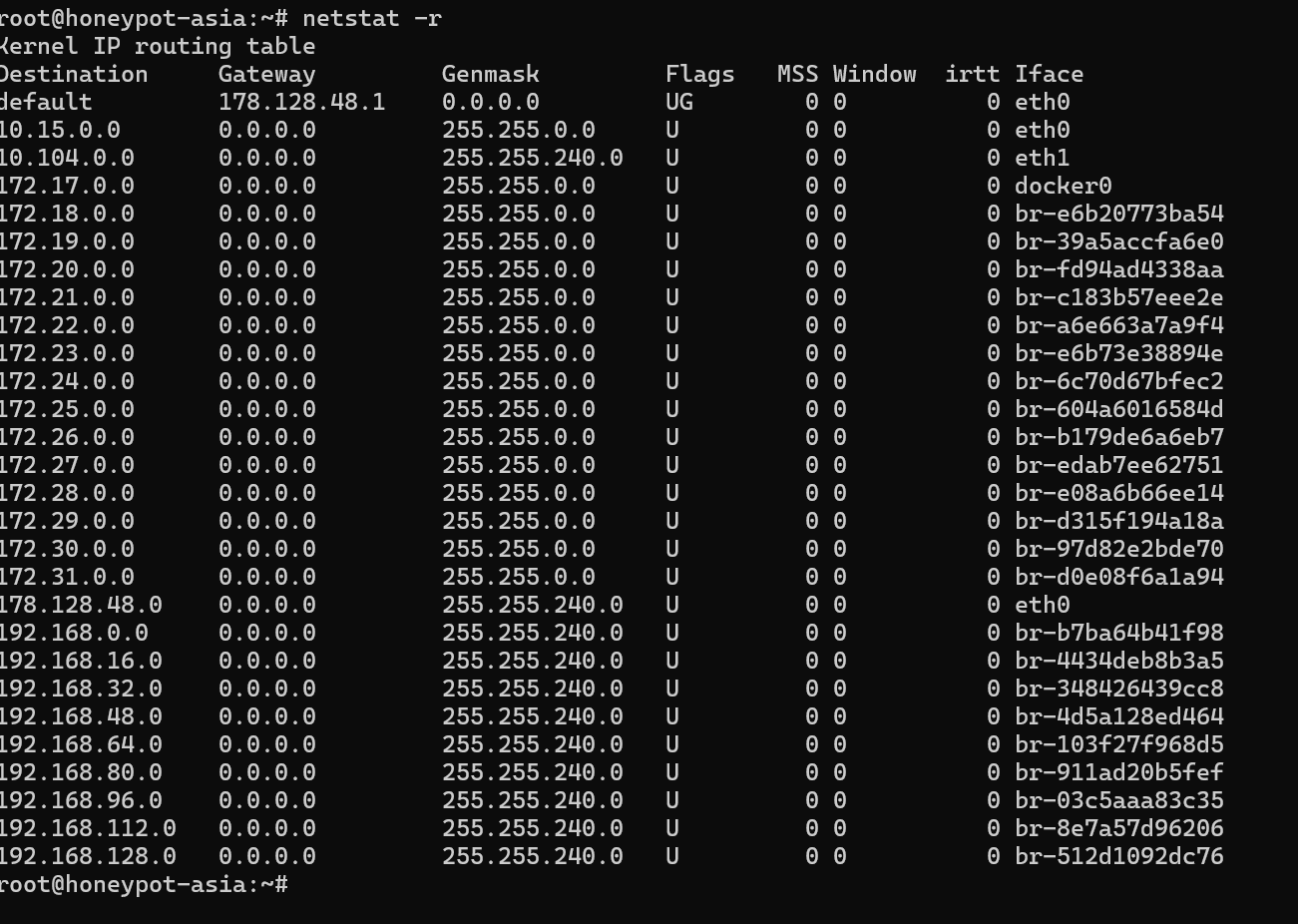
List Default Gateway netstat -r shows you the "map" that your computer uses to decide where to send network traffic. It lists:
- Gateway: The next stop for your data.
Interface: The network card used to send the data.
netstat -r
Advanced Options for Linux Investigations For more detailed analysis, especially in cases of network forensics or system investigations, netstat provides several advanced options:
netstat -tulnp
This powerful command combines several flags:
- -t: Displays TCP connections.
- -u: Shows UDP connections.
- -l: Lists only listening sockets.
- -n: Uses numerical addresses (avoidingDNS resolution).
- -p: Reveals the PID and name of the program using the socket.
Practical Tips for Linux Network Forensics
Filtering Output: Utilize text processing tools like grep to focus on particular ports or IP addresses. For example:
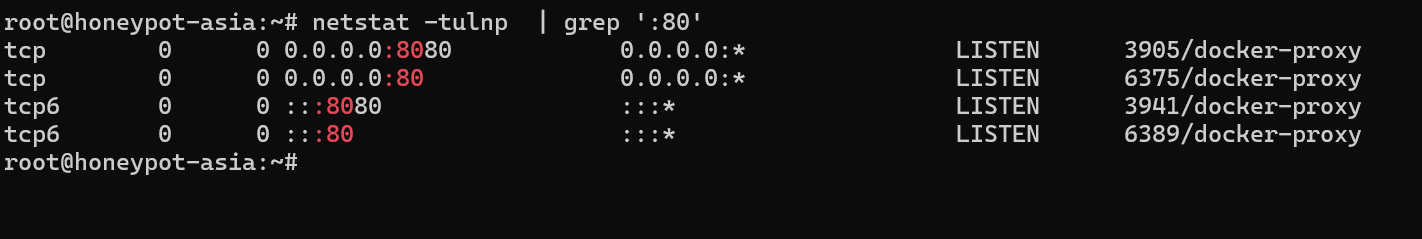
netstat -tulnp | grep ':80'
Conclusion
In this article we discussed the netstat command in Linux which is like a special tool that helps you see how your computer connects to the internet. While we've covered some common netstat options, there are many more that can tailor the output to your needs. For instance, the -i option displays network interface statistics, providing insights into the performance of each interface. Additionally, you can pipe netstat's output to utilities like more or less to paginate the results, making it easier to review without getting overwhelmed by long lists of data. This flexibility allows you to focus on the information most relevant to your investigation or troubleshooting task.

